The Right Method For Your MSP Success
Provide the World Class service that differentiates you from your competitors by leveraging our powerful combination of software, training and community.
Powerful Software To Build
Client Strategy
myITprocess™ allows you to develop a repeatable client process that is the basis for high-value relationships.
- Build comprehensive IT standards
- Access a library of industry compliance guidelines
- Complete impact assessments
- Deliver a strategic roadmap to every client
The combination of better real-time insight into your clients’ technology and better management of your own processes will enable you to deliver high-value vCIO relationships.

Proven Framework To Grow
Your Revenue
When you support myITprocess™ software with our TruMethods Framework training, you can:
- Close more sales
- Improve client retention
- Increase the prices you charge
- Grow your overall MRR (monthly recurring revenue)
Stay up to date with the constant fast-moving changes in technology, which affect both the services you provide and your own operations, by relying on TruMethods.
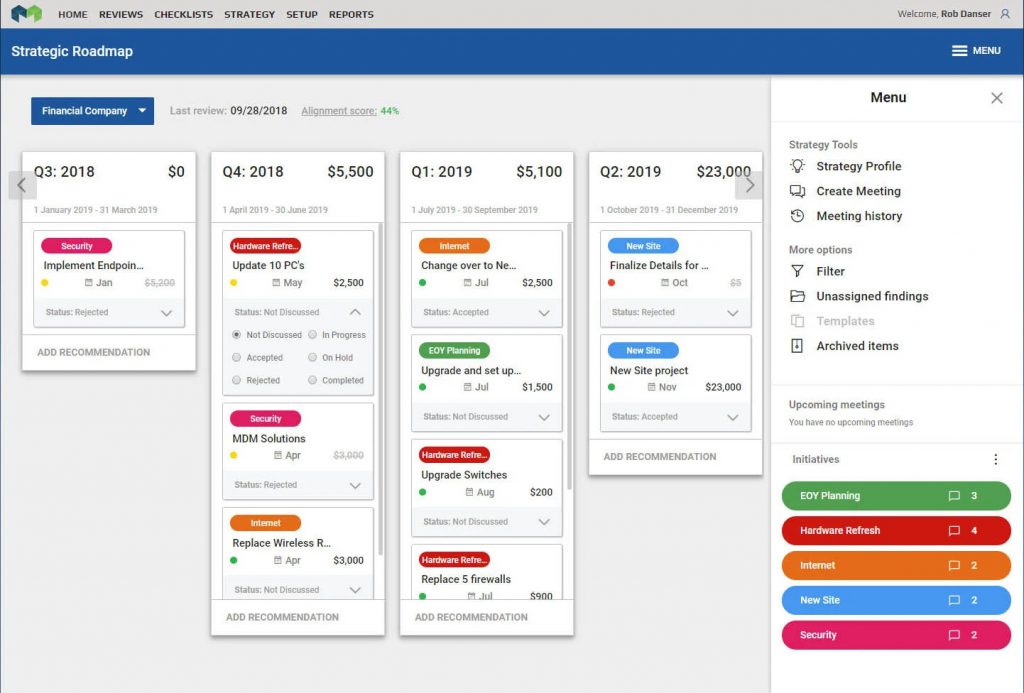
A Dynamic Combination
myITprocess™ gives you an in-depth view of both your clients’ systems and your own business. Use it in tandem with the proven strategies of our TruMethods Framework to achieve dramatic growth in revenue and profits, even while serving fewer clients.
Learn how to attract and retain high-value clients in your free guide,
How To Become A Top-Performing MSP.

Our Approach Helps Grow Your Revenue
Make Your MSP More Profitable
Get an expert diagnosis and three recommendations for improving your bottom line.
